Why Cybersecurity Training Is Essential for Every Employee in the USA cannot be overstated in today’s increasingly connected world. With cyber threats evolving at an alarming rate, businesses face unprecedented challenges in protecting sensitive data and maintaining trust. According to recent studies, 95% of cybersecurity breaches are caused by human error, highlighting the critical need for ongoing employee education. Organizations that invest in cybersecurity training empower their workforce to identify and respond to potential threats, reducing the risk of costly breaches and regulatory fines. In this blog, we will explore why cybersecurity training is essential, the benefits it provides to businesses, and actionable steps to create an effective training program that ensures data security and compliance.
Table of Contents
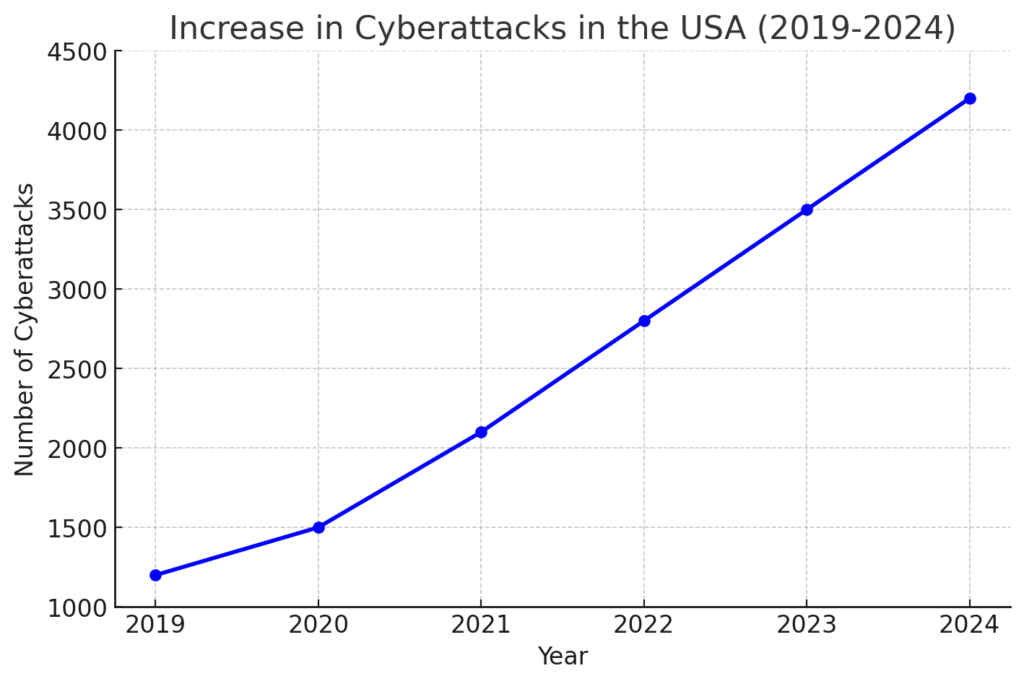
The Growing Threat of Cyber Attacks in the USA
Cyberattacks have been rising steadily, affecting organizations in various industries. In recent years, high-profile breaches have cost companies millions of dollars and damaged reputations.
- Statistics on recent cyberattacks in the USA.
- Common types of attacks (phishing, ransomware, insider threats).
- The financial and reputational impact on businesses.
How Cybersecurity Training Protects Businesses
Cybersecurity training equips employees with the knowledge to identify and respond to threats effectively. Proper training can:
- Reduce the risk of phishing and social engineering attacks.
- Enhance awareness of data protection policies.
- Improve incident response and reporting.

Here’s a step-by-step guide to identifying phishing emails along with examples of suspicious email elements:
Step 1: Check the Sender’s Email Address
- What to look for:
- Fake email addresses that resemble legitimate ones but contain slight variations (e.g.,
support@amaz0n.cominstead ofsupport@amazon.com). - Unfamiliar or misspelled domain names.
- Public email domains like
@gmail.comor@yahoo.comused by supposed official organizations.
- Fake email addresses that resemble legitimate ones but contain slight variations (e.g.,
Step 2: Examine the Subject Line
- What to look for:
- Urgent or threatening language such as “Your account has been compromised” or “Immediate action required.”
- Poor grammar or overly generic subjects like “Important Notification.”
Step 3: Inspect Links Before Clicking
- What to look for:
- Hover over links (without clicking) to see if the actual URL matches the displayed text.
- Links containing strange characters, long strings, or misspelled domain names.
- Links leading to non-secure HTTP websites instead of HTTPS.
Step 4: Look for Unsolicited Attachments
- What to look for:
- Attachments with unfamiliar or suspicious file extensions like
.exe,.zip,.pdf, or.docm. - Files named generically, such as “Invoice” or “Payment Details,” especially if unexpected.
- Emails claiming you must download attachments to avoid penalties.
- Attachments with unfamiliar or suspicious file extensions like
Step 5: Analyze the Email Content
- What to look for:
- Poor grammar, spelling errors, and awkward phrasing.
- Requests for sensitive information like passwords, bank details, or personal data.
- Greetings that are overly generic, such as “Dear Customer” instead of using your name.
Step 6: Verify Company Logos and Branding
- What to look for:
- Low-quality or pixelated logos and images.
- Formatting inconsistencies compared to official emails from the company.
- Fake contact information or missing official social media links.
Step 7: Trust Your Instincts and Report Suspicious Emails
- What to do:
- If something feels off, avoid interacting with the email.
- Report phishing emails to your company’s IT department or the Anti-Phishing Working Group (APWG).
- Delete the suspicious email immediately.
Key Elements of an Effective Cybersecurity Training Program
A robust cybersecurity training program should include:
- Awareness of common cyber threats.
- Secure password practices and multi-factor authentication.
- Recognizing suspicious activity.
- Regular updates and refresher courses.
Regulatory Compliance and Legal Implications
In the USA, businesses must comply with various regulations such as:
- GDPR (for companies dealing with EU customers).
- HIPAA (for healthcare organizations).
- CCPA (for companies handling California residents’ data).
Non-compliance can result in heavy fines and legal actions.

The Role of Leadership in Cybersecurity Training
Leadership plays a crucial role in fostering a security-conscious culture within an organization by:
- Setting an example by following cybersecurity best practices.
- Investing in continuous training programs.
- Encouraging employees to report suspicious activity without fear.
Common Cybersecurity Mistakes Employees Make
Despite training, common mistakes include:
- Using weak passwords.
- Clicking on suspicious links.
- Ignoring security updates.
How to Implement Cybersecurity Training Effectively
Tips for successful implementation:
- Use engaging, interactive modules.
- Conduct regular assessments.
- Provide incentives for compliance.
The Financial Benefits of Cybersecurity Training
Investing in cybersecurity training can lead to:
- Reduced costs related to data breaches.
- Lower insurance premiums.
- Improved customer trust and business reputation.
Conclusion: Why Cybersecurity Training Is Essential for Every Employee in the USA
In today’s ever-evolving digital landscape, cybersecurity training is essential for every employee in the USA. With cyber threats becoming more sophisticated and frequent, businesses cannot afford to overlook the importance of equipping their workforce with the necessary skills to recognize and mitigate potential risks. Studies show that organizations with robust cybersecurity training programs experience 70% fewer security breaches compared to those without proper training. Investing in cybersecurity training not only enhances data protection but also helps businesses comply with regulatory requirements and build a culture of security awareness.
To stay ahead of cyber threats, businesses must prioritize regular cybersecurity training and ensure employees are well-versed in best practices. Every employee in the USA plays a crucial role in safeguarding sensitive information and protecting the organization from potential cyberattacks.
Call-to-Action:
Encourage businesses to implement regular cybersecurity training and stay proactive against evolving threats. [TechGeniuxio.com]





